
By TJ Null, Offensive Security Community Manager
Over the last few years, PowerShell has become a powerful scripting language for automating the system administration and applications running on Windows. Microsoft has also made PowerShell available for non-Windows platforms using .NET Core. Recently, Offensive Security added PowerShell to Kali Linux.
Using PowerShell on Linux can provide a variety of benefits including:
- Writing and debugging scripts in PowerShell
- Connecting to Windows targets
- Transferring files
However, there are some things that are currently missing in PowerShell for Linux, such as:
- Unsupported cmdlets
- Ability to use sudo or exec directly in PowerShell
- Support for WMI or CIM
In this piece, we will demonstrate how to obtain a PSSession from our Kali System to our targets (Windows and Linux). In PowerShell, the PSSession cmdlet allows us to create a persistent connection to a local or remote computer. Using PSSession gives us the ability to interact with our targets while encrypting all transmitted content.
Note: These techniques were tested on Windows 10 x64 Pro, version 2004, and Ubuntu 20.04 LTS.
Jump to: Obtaining a PSSession on Windows | Obtaining a PSSession on Linux | Obtaining a Reverse Shell from PowerShell on Linux | Taking Reverse Shells Further
OBTAINING A PSSESSION ON WINDOWS
To interact with a PSSession, our Windows target must have PSremoting enabled and have credentials to access the system. When you enable PSRemoting, it uses the default HTTP 5985 port for connection. SSL is not enabled by default because WS-Management encrypts all Windows PowerShell content transmitted over the network in our PSSession. For this scenario, we are going to stick with the default options.
On our Kali System, the Powershell for Linux package needs to have a separate package installed and some configurations changed in order for us to obtain a PSSession. We will need to install gss-ntlmssp and create two symlinks in the PowerShell directory to ensure the WSman module in PowerShell is working correctly. At this time, the PowerShell team has not yet implemented this fix. We hope that they will do so in the next release.
In this case, our PowerShell is located in the following path:
/opt/microsoft/powershell/7
Navigate to the directory above. In that directory, we need to add our symlinks:
ln -s /usr/lib/x86_64-linux-gnu/libcrypto.so.1.0.2 libcrypto.so.1.0.0
Now that we have made these changes, let’s create our first PSSession. On our Kali system in our PowerShell terminal, we will type this command to create our new PSSession.
Using the proper credentials, we should be able to interact with our Windows target in the PSSession. As you can see in the screenshot below, we were successfully able to obtain a PSSession on our Windows target.
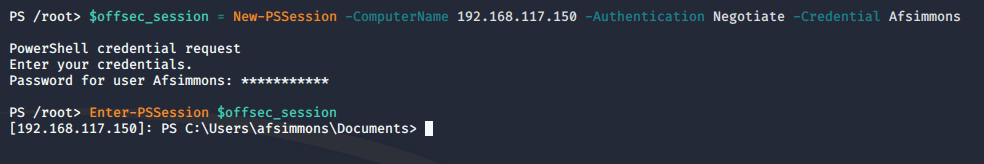
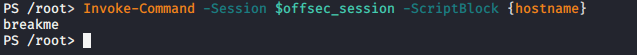
If we decide to exit our PSSession, we can continue to interact with the remote host by using the “Invoke-Command†cmdlet to execute any commands or scripts in our session. In addition, we can also use the Invoke-Command to run a single command on multiple computers if we have access to them. To demonstrate, let’s create a script block to run the hostname command on our target. The command we will use is:
Invoke-Command -Session $offsecsession -ScriptBlock {hostname}
Read More . . . ! ! !
*Beware click the link!

 Murtad methamphetamine
Murtad methamphetamine
 Sandidi
Sandidi
 ImamWawe
ImamWawe

