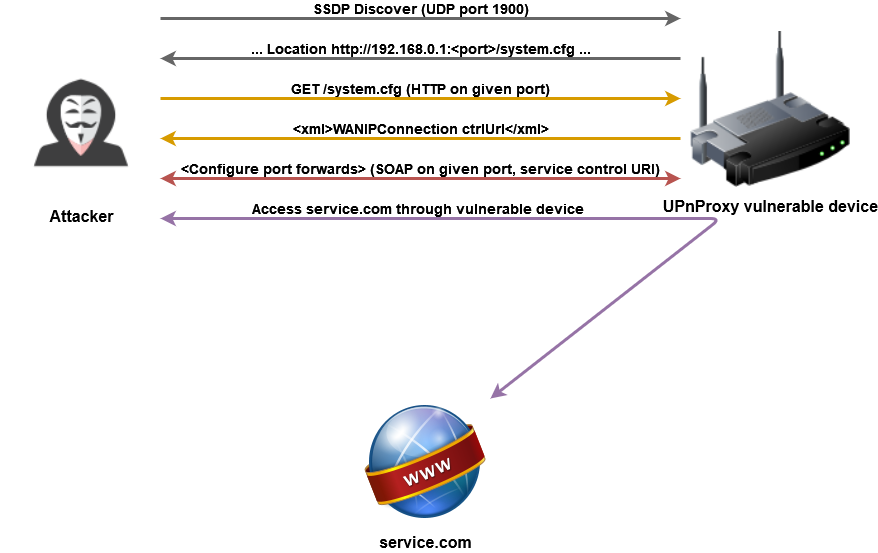
UPnProxyChain: a Tool to Exploit Devices Vulnerable to UPnProxy
How it works
The tool will send an SSDP discover message to the target host to discover its UPnP services. Target host with flawed UPnP implementation will respond with a URI pointing to a document describing its services.
The tool will then download the document, figure if the target is offering either WANPPPConnection or WANIPConnection service, and if so, start controlling the service to inject routes.
A device may not respond to UDP discover message even though it is exploitable. For those cases, UPnProxyChain will try to guess popular UPnP ports and URIs of service description documents and go from there.
Some devices are vulnerable but are not exploitable because they have a firewall blocking usage of any additional ports.
Read more : https://shufflingbytes.com/posts/upnproxychain-a-tool-to-exploit-devices-vulnerable-to-upnproxy/
*Beware click the link!

 Murtad methamphetamine
Murtad methamphetamine
 Sandidi
Sandidi
 ImamWawe
ImamWawe


