Hallo there
I have found this https://github.com/Jieyab89/OSINT-Cheat-sheet, https://github.com/zelsaddr/OSINT-Cheat-sheet-. I have searched for the owner of this repo in this repo there are things that I'm interested in and have questions
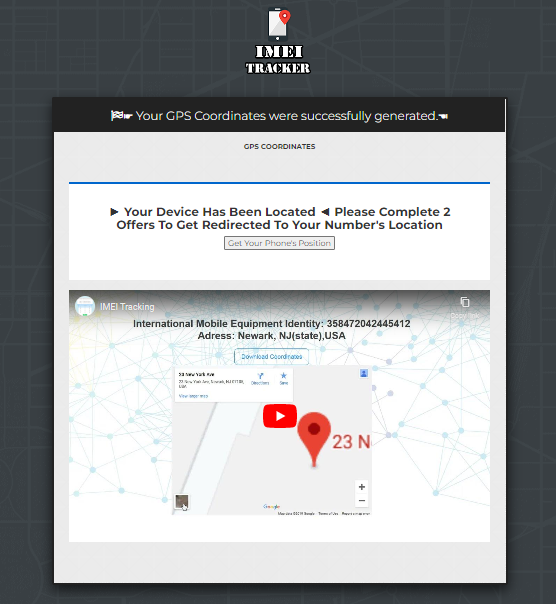
this site https://www.airdroid.com/parent-control/how-to-track-phone-using-imei-online/ & imei-tracker.com explains how to track a mobile phone by IMEI from what I read and searched know I'm still having trouble and struggling understanding about this. Here is my question
1. Can this site imei-tracker.com site do this?
2. Can anyone track IMEI with a third party website or IMEI tracker service?
3. Tracking the phone number and IMEI is same method?
4. Can IMEI be changed? How?
5. How to track my lost phone without using IMEI and phone number?
6. Is there hardware and software to track IMEI?
Can someone help me understand mobile tracking by localization
*Beware click the link!




 Murtad methamphetamine
Murtad methamphetamine
 Sandidi
Sandidi
 ImamWawe
ImamWawe
Freelance | Student
Probably, im not sure answer this im still research, read and learn about signal and GSM and others. Correct me if there is any wrong information (CMIW) I will answer your question. IMEI is a unique 15-digit number that is used for serialization on the device you are using, for example smartphones, laptops and hardware to see date purchase, device information, warranty, when the device is turned on or active and so on, In my country there are institutions from the government that can do this, for example "kominfo, police, provider, bea cukai" The Central Equipment Identity Register (CEIR) will help those whose mobiles are lost or stolen, as they will be able to inform the Department of Telecom (DoT) via a helpline number after filing a report with the police.
1. Can this site imei-tracker.com site do this?
No, and I have never tried with this (beware scam) I just try to see device details but not to the location only basic information
example
you can see in my repository (imei check) if you want to believes please try on the site (imei-tracker.com) try itself
2. Can anyone track IMEI with a third party website or IMEI tracker service?
Maybe, you can track with sites or services that have collaborated with governments, operators and others. But this requires strict permits and authorization. Can't do something like that easily or without permission because it's about privacy
3. Tracking the phone number and IMEI is same method?
From what I've read and I understand these are related, Operators can do ISD, HLR, SRI-SM. SRI (sent routing info) for SM (sort message) is the reapon from HLR (home location register) to SMC (sort message service center) using tower triangulation (BTS) to find. You cannot ask the operator to provide you with a location report. Phone company or provider does all the tracking when someone calls your cell phone number, the cell phone system already knows where you are this is a built in function of the tower (BTS) Whenever there is a phone call, call details are recorded by service provider (operator) So when you call someone or receive a call all call related details like call duration, caller info, phone number, IMEI number and location area code will be recorded at the nearest cell tower You can read about Triangulation, Trilateration, Multilateration. Agencies, providers or operators and hackers (maybe) have the ability to do that
*IMEI pinning is possible when the stolen phone is activated (powered on). If the phone is not activated, we can deal with the final stages of the phone (last location) At the last stage you will be able to know where the phone was deactivated (powered off).
4. Can IMEI be changed? How?
Idk, I haven't done this in practice, but from what I've read it does, you can change your IMEI
https://www.cashify.in/how-to-change-the-imei-number-on-my-smartphone
5. How to track my lost phone without using IMEI and phone number?
Hmmmmm, i think spying (monitoring) apps which can be installed on phone, email like i cloud, find my phone and other, but if you lost phone you can try this procedure
- Prepare a copy of the IMEI number that you have saved.
- Contact the call center or operator according to the cellphone brand you are using or call the police.
- Tell them you have lost your phone and give them the IMEI number.
- After that, the operator will track if your IMEI number unit is found.
if your phone is stolen or lost, you should report it to your operator and police by telling them your manufacturer, model, imei number, color, some specialrecognizable details (if any), place and date where it was stolen and some other circumstances that could help them to find or locate your mobile phone
6. Is there hardware and software to track IMEI?
You can search itself :D
I can't answer in detail here because it might harm me or this forum, I can't answer for sure and in detail and I'm not 100% sure of what I wrote, if there's something wrong, please correct it. Thakns for visiting my github repo don't forget give it stars and share w your firends. You can read on this
*Note
My advice, don't trust IMEI location tracking sites, phone number track location sites. I don't know this in depth, if my answer is lacking or you still curious. You try to ask people like security forces, employee at the operator (provider), telco, gsm cell, RF. This is a tricky question for me. OSINT is not easy, moreover it includes signaling (SIGINT and ELINT) and others where we do not have full authority access to what we want to search for. Hope this helps, this is a recommendation from me that I've read in the past
- https://www.seminarsonly.com/Labels/Sniffer_for_detecting_lost_mobiles.php
- https://sci-hub.se/https://ieeexplore.ieee.org/document/7345408
- https://indianexpress.com/article/technology/mobile-tabs/imei-number-india-track-stolen-mobiles-phones-how-to-find-imei-what-it-does-5790035/
- https://sci-hub.se/https://ieeexplore.ieee.org/abstract/document/8769521
- https://sci-hub.se/https://ieeexplore.ieee.org/abstract/document/9012000
- https://en.wikipedia.org/wiki/Cell_of_origin
- https://forum.seccodeid.com/d/apa-itu-imsi
- https://commons.lib.jmu.edu/cgi/viewcontent.cgi?article=1013&context=master201019
Reply
Reply
In my region this called ‘ladusing’
Reply
Lol i see what you mean
Reply
Reply
Block IMEI so that thief cannot use operator services, ISILOP indonesia can actually do it by working with operators as evidence of cases such as the red kebaya, bully artists, presidents, agencies. The actor can be tracked and the perpetrators found, you can understand this how they serve us, not only you i have also lost my smartphone
Reply
Thank for your answer i was read your references, but i have other question here
1. Are calls like gsm and cdma encrypted? For example, if I call my mom, then is the cellular call encrypted? And people like cake operator providers,
i.e verizon, NTT docomo, etc can recognize the chat?
2. Complementary relationship among SIGINT and ELINT
3. How do hackers and terrorists avoid tracking and evading?
Reply
1. Are calls like gsm and cdma encrypted? For example, if I call my mom, then is the cellular call encrypted? And people like cake operator providers,
i.e verizon, NTT docomo, etc can recognize the chat?
The call, SMS is not encrypted, it is clear that the call can be known by the provider, the contents of the package. But not saved. If you've ever heard of
SS7 (protocol there are five layers, this is OSI on telco) SS7 is an old technology, while SS7 was the foundation for signaling in 2G/3G circuit switch networks and it will not be used anymore in the future, now it is being replaced by volte like 4g and LTE
voice over data (read on bottom link)
Hint : You can use sigploit tool, SDR and wireshark to intercept TCAP
*I don't much understand this telco
2. Complementary relationship among SIGINT and ELINT
Signals Intelligence (SIGINT) is intelligence-gathering by interception of signals, both communication signals between people (communication intelligence - abbreviated as COMINT) and from electronic signals that are indirectly used in communication (electronic intelligence - abbreviated as ELINT).
Signal intelligence is a subset of intelligence gathering management. Sensitive information is often encrypted, so signal intelligence eventually involves using cryptanalysis to decipher encrypted messages.
Electronic signal intelligence (ELINT) refers to intelligence-gathering using electronic sensors. Its main focus lies on non-communication signal intelligence
The data collected is usually related to the electronics of adversary defense networks, especially electronic parts such as radars, surface-to-air missile systems, aircraft.
ELINT can be used to detect ships and aircraft with their radar and other electromagnetic
Conclusion:
ELINT allows traffic analysis to be performed on electronic emissions that contain human encoded messages. The analysis method is different from SIGINT analyze radio transmission and its position through triangulation
Other ELINTs include intercepting and analyzing signals
3. How do hackers and terrorists avoid tracking and evading?
Idk, I haven't research much about this, just wait, maybe someone will answer
I want to ask you, from what I have read and analyzed, have you learn OSINT before? looks like you've learned this before
Read on here
- https://www.fcc.gov/general/voice-over-internet-protocol-voip
- https://www.zdnet.com/article/5g-networks-could-be-vulnerable-to-exploit-due-to-mishmash-of-old-technologies/
- https://www.bleepingcomputer.com/news/security/most-ss7-exploit-service-providers-on-dark-web-are-scammers/
- https://blog.mobileum.com/mobile-volte-fraud
- https://www.efani.com/blog/ss7-attack
- https://www.cellusys.com/2019/08/29/what-is-tcap/
- https://www.nsa.gov/portals/75/documents/about/cryptologic-heritage/historical-figures-publications/publications/misc/elint.pdf
- https://id.wikipedia.org/wiki/SIGINT
- https://www.techtarget.com/whatis/definition/ELINT-electronic-intelligence
- https://en.wikipedia.org/wiki/Signals_intelligence
Reply
Nice question and answer. I also have a question!
1. Can apps like get contact and truecaller track locations?
2. If the government, the police can track locations such as imei, cell phone numbers and so on, why is it difficult for the public to request a report on this location
3. Can the Indonesian government trace locations to insiders or common people
4. Tracking method
Reply
Here the answers
1. Can apps like get contact and truecaller track locations?
Yes, if they ask you to access the location. Apps need permission to do this, as far as my experience with programming goes. An application or software cannot have location access without user permission, if without permission at most they parse data based on IP address, or even if they do so it would violate privacy. Or they can have a location if they work with related providers such as providers or carriers, but this is not possible because it requires permission and not just anyone can have this permission. This kind of authority, in my opinion, is a special organization
2. If the government, the police can track locations such as imei, cell phone numbers and so on, why is it difficult for the public to request a report on this location
Hmmm, idk
3. Can the Indonesian government trace locations to insiders or common people
I do not understand the meaning of this question. This is what I caught from question number 3. The Indonesian government can do this, they can request access from the provider to get location data or cooperate, this is used for crime, some governments or people who have authority can do this. Providers can help because they have access to this
4. Tracking method
You can search "triangulasi" or "Cell Phone Circuit" or "SIGINT" try it yourself :D or you can try hack the operator to gett accsess
Reply
Related w your post
https://medium.com/@ibederov_en/check-and-locate-phone-number-in-osint-8beb8af50d5e
https://hakin9.org/uncovering-data-from-phone-numbers/
Reply
Are you sure there is no encryption or a certain algorithm in it?
Other question!
Your answer there is a HLR I have tried this it only detects when and where it is activated then what data does the operator store in the HLR and stuff? Can you give more information about sigploit?
Reply
From what I have read and I understand the answer is yes. And I asked my friend he had worked at Indonesian operators or providers such as XL, Indosat, Telkomsel and had been the Head Network he called Syamsul. This is about the architecture inside cellular or telco. Example below:
- HLR (Home Location Register)
The Home Location Register (HLR) is the subscriber's database in the home network. Each subscriber is stored in only one HLR the operator may have more than one depending on number of subscribers. The HLR is responsible of holding the following information:
(1) User identification (IMSI) and Numbering
(MSISDN).
(2) User security information: Network access contral
information for authentication and authorization (K;, Ke).
(3) User location information: Mobile switching
centerNisitor location register (MSC/VLR), that a user is
currently attached to, as well as_ cell ID.
(4) User profile information: Services that the user is
subscribed to. For instance call forwarding, current
balance,.. etc. The HLR also generates user security
information for mutual authentication, communication
integrity check and ciphering
- VLR (Visitor Location Register)
A VLR is responsible for a specific region. Each subscriber traveling to a particular region is connected/attached to her VLR responsible for that region. The VLR acts as a temporary database for the duration of roaming subscribers. Has the same information as home network HLR
*Some I have explained in the previous comments
- MSC (Mobile Switching Center)
Cells (BTS towers) are connected to an MSC. The MSC is responsible for route and switch calls, SMS and data from and to the subscribers attached to it
*Some I have explained in the previous comments
- SMSC (Short Message Switching Centre)
Sending and delivering short messages (SMS) to subscribers
*Some I have explained in the previous comments
- STP (Signal Transfer Point)
Is a node in an SS7 network that routes signaling messages based on their destination point code in the SS7 network. Gateway (router) of the carrier, which is responsible for all routing, routing, and delivery of SS7 messages.
Detail info, you can read on botton link
Operators or providers have databases that store HLR customer information/profiles for each operator in only one HLR. The HLR stores important information including:
- Services like calls, SMS other things
- IMSI (International mobile subscriber identity)
- IMEI (International Mobile Equipment Identity)
- MSISDN (Mobile Station International Subscriber Directory Number)
- Last location
- Subscriptions
Read here
- https://dione.lib.unipi.gr/xmlui/handle/unipi/12489
- https://www.sciencedirect.com/science/article/pii/S0167404822004394 (SCI HUB CANT BYPASS)
- https://sci-hub.se/https://ieeexplore.ieee.org/document/8436820
- https://www.researchgate.net/publication/267409463_IMS_Signalling_in_LTE-based_Femtocell_Network
- https://repository.telkomuniversity.ac.id/pustaka/95715/analisis-kinerja-signaling-ims-yang-diterapkan-pada-jaringan-publik-ip-di-operator-telekomunikasi-berbasis-gsm-dan-cdma.html
- https://en.wikipedia.org/wiki/Signal_Transfer_Point
*Include about sigploit
Reply
You can learn arch on my reff
Reply