Case Summary
In this intrusion, a threat actor abused the CVE-2022-30190 (Follina) vulnerability, where exploit code was embedded inside a malicious Word document to gain initial access. We assess with medium to high confidence that the documents likely arrived by the means of thread-hijacked emails from distribution channels used by TA570.
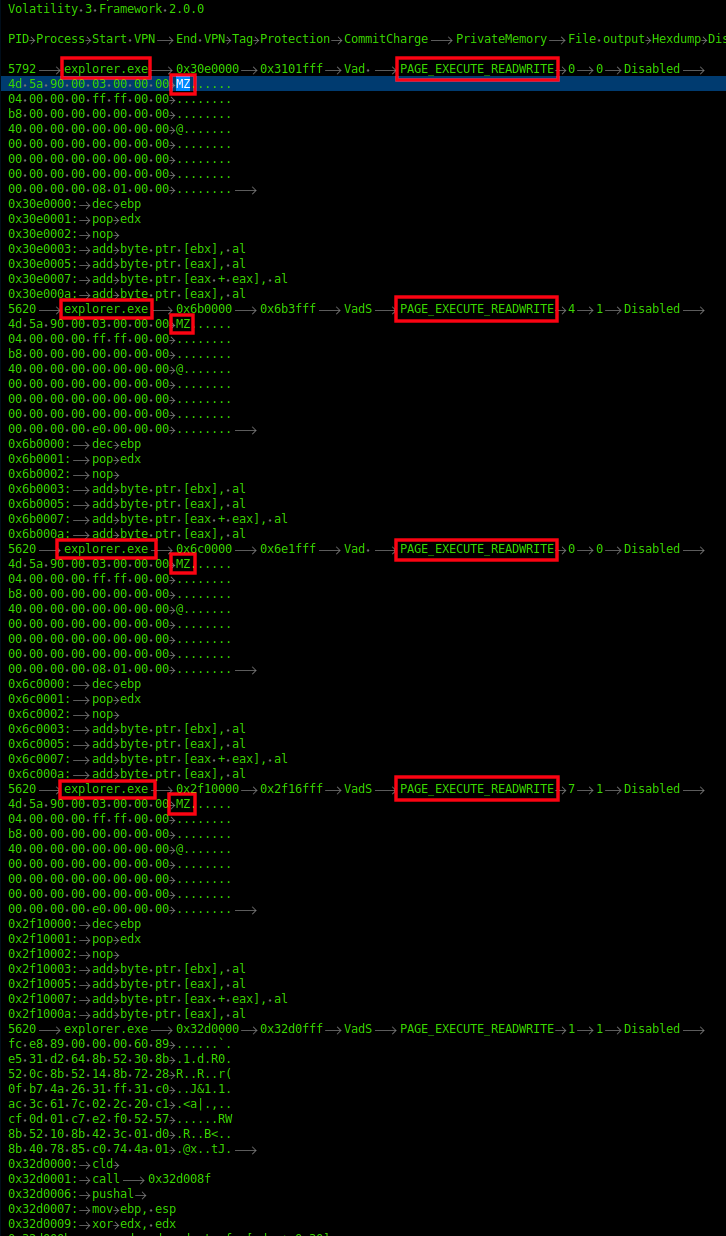
Upon execution of the weaponized Word document, a HTML file was retrieved from a remote server containing a PowerShell payload. The payload contains base64-encoded content and is used to download Qbot DLLs inside the user’s Temp directory. The Qbot DLL was executed via regsvr32.exe and the activity was immediately followed by injection into legitimate processes (explorer.exe) on the host.
The injected process spawned Windows utilities such as whoami , net.exe and nslookup, to perform discovery activity and also established connection to Qbot C2 servers. Almost an hour later, the threat actors leveraged a Windows built-in utility, esentutl.exe, to extract browser data, a technique also observed in earlier cases. [1][2]
Qbot used scheduled task creation as a persistence mechanism. The scheduled task contained a PowerShell command referencing multiple C2 IP addresses stored as base64-encoded blob in randomly named keys under the HKCU registry hive.
After this activity, the threat actor proceeded with the remote creation of Qbot DLLs over SMB on multiple hosts throughout the environment. They then added multiple folders to the Windows Defender exclusions list on each of the infected machines to evade defenses, as we have seen before with Qbot. Remote services were then used to execute the DLLs.
A Cobalt Strike server connection was witnessed within the first hour, but it wasn’t until after lateral movement occurred that activity from that server began. Utilities such as nltest.exe and AdFind were executed by the injected Cobalt Strike process (explorer.exe). The injected process was also used to access the LSASS system process. Then, the threat actors installed a remote management tool named NetSupport Manager. Within 20 minutes of the installation, the threat actor moved laterally to the domain controller via a Remote Desktop session.
On the domain controller, the tool Atera Remote Management was deployed, a popular tool used by attackers for controlling victim machines. This was the last adversarial activity observed for the day.
The threat actors checked-in early the next day and downloaded a tool named Network Scanner by SoftPerfect on a domain controller. The tool was executed, which ran a port scan across the network. Finally, the threat actors connected to one of the file share servers via RDP and accessed sensitive documents.
No further attacker activity was observed before the threat actors were evicted from the environment.
Indicators
www.stanzatextbooks[.]com www.framemymirror[.]com www.coolwick[.]com www.ajparts.co[.]uk incredibletadoba[.]com ibuonisani[.]it gruposolel[.]com foxmotorent[.]com egofit.co[.]uk edifica[.]ro dwm-me[.]com cursosfnn[.]com cemavimx[.]com atlasbar[.]net
Read more : https://thedfirreport.com/2022/10/31/follina-exploit-leads-to-domain-compromise/
*Beware click the link!
 Djie sam soe
Djie sam soe
 Murtad methamphetamine
Murtad methamphetamine
 ImamWawe
ImamWawe
